Amazon CodeGuru allows you to automate code reviews and improve code quality, and thanks to the new pricing model announced in April you can get started with a lower and fixed monthly rate based on the size of your repository (up to 90{835c7ebc5b9c2482a00818e88912716a918901c7fd3f141d94f121bbdc6c5073} less expensive). CodeGuru Reviewer helps you detect potential defects and bugs that are hard to find in your Java and Python applications, using the AWS Management Console, AWS SDKs, and AWS CLI.
Today, I’m happy to announce that CodeGuru Reviewer natively integrates with the tools that you use every day to package and deploy your code. This new CI/CD experience allows you to trigger code quality and security analysis as a step in your build process using GitHub Actions.
Although the CodeGuru Reviewer console still serves as an analysis hub for all your onboarded repositories, the new CI/CD experience allows you to integrate CodeGuru Reviewer more deeply with your favorite source code management and CI/CD tools.
And that’s not all! Today we’re also releasing 20 new security detectors for Java to help you identify even more issues related to security and AWS best practices.
A New CI/CD Experience for CodeGuru Reviewer
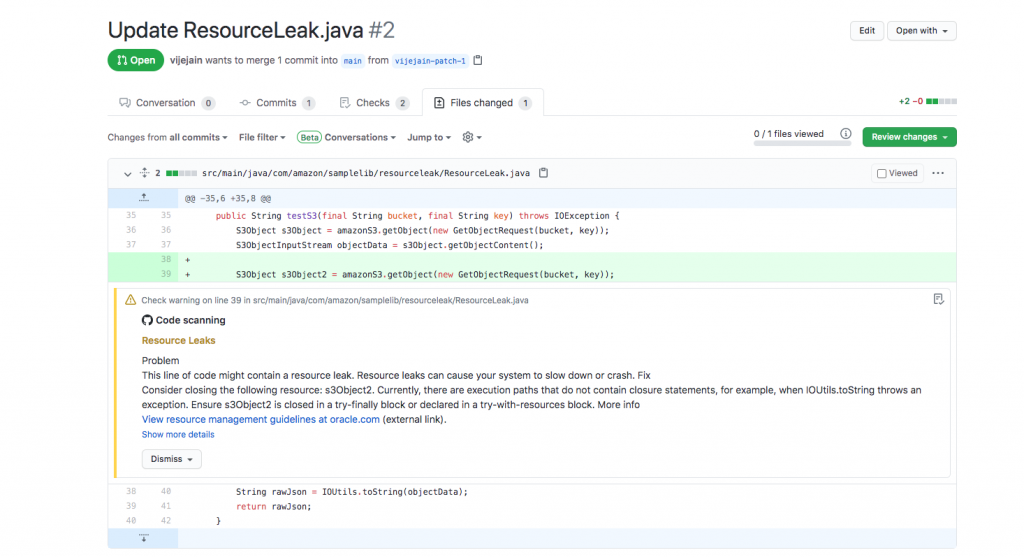
As a developer or development team, you push new code every day and want to identify security vulnerabilities early in the development cycle, ideally at every push. During a pull-request (PR) review, all the CodeGuru recommendations will appear as a comment, as if you had another pair of eyes on the PR. These comments include useful links to help you resolve the problem.
When you push new code or schedule a code review, recommendations will appear in the Security > Code scanning alerts tab on GitHub.
Let’s see how to integrate CodeGuru Reviewer with GitHub Actions.
First of all, create a .yml file in your repository under .github/workflows/ (or update an existing action). This file will contain all your actions’ step. Let’s go through the individual steps.
The first step is configuring your AWS credentials. You want to do this securely, without storing any credentials in your repository’s code, using the Configure AWS Credentials action. This action allows you to configure an IAM role that GitHub will use to interact with AWS services. This role will require a few permissions related to CodeGuru Reviewer and Amazon S3. You can attach the AmazonCodeGuruReviewerFullAccess managed policy to the action role, in addition to s3:GetObject, s3:PutObject and s3:ListBucket.
This first step will look as follows:
- name: Configure AWS Credentialsn uses: aws-actions/configure-aws-credentials@v1n with:n aws-access-key-id: ${{ secrets.AWS_ACCESS_KEY_ID }}n aws-secret-access-key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}n aws-region: eu-west-1nThese access key and secret key correspond to your IAM role and will be used to interact with CodeGuru Reviewer and Amazon S3.
Next, you add the CodeGuru Reviewer action and a final step to upload the results:
- name: Amazon CodeGuru Reviewer Scannern uses: aws-actions/codeguru-reviewern if: ${{ always() }} n with:n build_path: target # build artifact(s) directoryn s3_bucket: 'codeguru-reviewer-myactions-bucket' # S3 Bucket starting with "codeguru-reviewer-*"n- name: Upload review resultn if: ${{ always() }}n uses: github/codeql-action/upload-sarif@v1n with:n sarif_file: codeguru-results.sarif.jsonThe CodeGuru Reviewer action requires two input parameters:
-
- build_path: Where your build artifacts are in the repository.
-
- s3_bucket: The name of an S3 bucket that you’ve created previously, used to upload the build artifacts and analysis results. It’s a customer-owned bucket so you have full control over access and permissions, in case you need to share its content with other systems.
Now, let’s put all the pieces together.
Your .yml file should look like this:
name: CodeGuru Reviewer GitHub Actions Integrationnon: [pull_request, push, schedule]njobs:n CodeGuru-Reviewer-Actions:n runs-on: ubuntu-latestn steps:n - name: Configure AWS Credentialsn uses: aws-actions/configure-aws-credentials@v1n with:n aws-access-key-id: ${{ secrets.AWS_ACCESS_KEY_ID }}n aws-secret-access-key: ${{ secrets.AWS_SECRET_ACCESS_KEY }}n aws-region: us-east-2n - name: Amazon CodeGuru Reviewer Scannern uses: aws-actions/codeguru-reviewern if: ${{ always() }} n with:n build_path: target # build artifact(s) directoryn s3_bucket: 'codeguru-reviewer-myactions-bucket' # S3 Bucket starting with "codeguru-reviewer-*"n - name: Upload review resultn if: ${{ always() }}n uses: github/codeql-action/upload-sarif@v1n with:n sarif_file: codeguru-results.sarif.jsonnIt’s important to remember that the S3 bucket name needs to start with codeguru_reviewer- and that these actions can be configured to run with the pull_request, push, or schedule triggers (check out the GitHub Actions documentation for the full list of events that trigger workflows). Also keep in mind that there are minor differences in how you configure GitHub-hosted runners and self-hosted runners, mainly in the credentials configuration step. For example, if you run your GitHub Actions in a self-hosted runner that already has access to AWS credentials, such as an EC2 instance, then you don’t need to provide any credentials to this action (check out the full documentation for self-hosted runners).
Now when you push a change or open a PR CodeGuru Reviewer will comment on your code changes with a few recommendations.

Or you can schedule a daily or weekly repository scan and check out the recommendations in the Security > Code scanning alerts tab.

New Security Detectors for Java
In December last year, we launched the Java Security Detectors for CodeGuru Reviewer to help you find and remediate potential security issues in your Java applications. These detectors are built with machine learning and automated reasoning techniques, trained on over 100,000 Amazon and open-source code repositories, and based on the decades of expertise of the AWS Application Security (AppSec) team.
For example, some of these detectors will look at potential leaks of sensitive information or credentials through excessively verbose logging, exception handling, and storing passwords in plaintext in memory. The security detectors also help you identify several web application vulnerabilities such as command injection, weak cryptography, weak hashing, LDAP injection, path traversal, secure cookie flag, SQL injection, XPATH injection, and XSS (cross-site scripting).
The new security detectors for Java can identify security issues with the Java Servlet APIs and web frameworks such as Spring. Some of the new detectors will also help you with security best practices for AWS APIs when using services such as Amazon S3, IAM, and AWS Lambda, as well as libraries and utilities such as Apache ActiveMQ, LDAP servers, SAML parsers, and password encoders.

Available Today at No Additional Cost
The new CI/CD integration and security detectors for Java are available today at no additional cost, excluding the storage on S3 which can be estimated based on size of your build artifacts and the frequency of code reviews. Check out the CodeGuru Reviewer Action in the GitHub Marketplace and the Amazon CodeGuru pricing page to find pricing examples based on the new pricing model we launched last month.
We’re looking forward to hearing your feedback, launching more detectors to help you identify potential issues, and integrating with even more CI/CD tools in the future.
You can learn more about the CI/CD experience and configuration in the technical documentation.
— Alex